Do you want to bypass firewalls and have access to all blocked content? This guide will put you through the various methods you can use to bypass firewalls without stress.
What is a Firewall?
It’s a security system that is often used to track every outgoing and incoming network traffic. It can decide to block or enable particular traffic according to a specific form of advanced security rules.
Firewalls were first used as far back as twenty-five years. They were first used as the initial defense line in network security. As of now, they are still very useful in terms of improving your computer’s security that is linked to networks like the internet network or a LAN.
You can use firewalls for controlling and managing traffic, for reporting and recording events, for validating access and defending resources.
However, as the firewalls secure your computer network, they often still become unbearable for both students and employees who find it difficult to gain access to the sites of their choice like streaming services, social media platforms, etc.
Various Ways You Can Bypass Firewall
Navigation of Contents
Now that we have looked into what a firewall is, you might feel that it’s impossible or hard to bypass the in order to gain access to any website of your choice. Fortunately, there’re various means you can use to circumvent firewalls and access your favorite sites. You may find some of these ways effective and cheap. We will examine the various means of bypassing a firewall below.
1. Bypass a firewall using Ultrasurf
One of the first means of bypassing a firewall is by using Ultrasurf that makes use of the default browser of a computer in order to connect to the closest proxy. It works by opening an incognito window in the computer browser. After this, it grants you access to blocked sites via the proxy server.
The fact that Ultrasurf does not need to be installed enables you to use it on a completely restricted device. The only negative thing about it is that it can only be used on Windows computers. This means that users of Mac devices will have to use make use of other means.
2. Bypass a Firewall by Browsing with Tor
Another means of bypassing a firewall is by browsing with Tor. It is one of the most well-known web browsers. It enables you to browse the internet without revealing your identity or information.
Tor helps you to route the web browsing over a network that is encrypted. After this, it sends a request to you to an unfiltered and uncensored destination. You can use Tor to gain access to restricted sites using any connection. Note that you must not use it to access unencrypted and sensitive data.
Despite the fact that Tor is very useful in places where proxies, Virtual Private Networks (VPNs), and SSH tunnels wouldn’t work, it still has its disadvantage. One of these disadvantages is that it is effectively slow. This means that even if Tor grants you access to restricted sites, you might not have the patience to wait for long.
3. Bypass a Firewall using your mobile phone
This method of bypassing a firewall is by using your mobile phone. In case your mobile phone allows you to use your cellular data to connect to Wi-Fi on a PC, then you can bypass a firewall through the following means:
- The first thing to do is to switch off the Wi-Fi of your mobile phone.
- After this, connect the charger of your mobile phone to your phone and your computer.
- Once you have done that, you will have to turn on the hotspot of your mobile phone.
- After that, go to your PC and select your mobile phone as the internet network connection.
By connecting the internet connection of your mobile to your computer, you can now bypass any firewall without any issue.
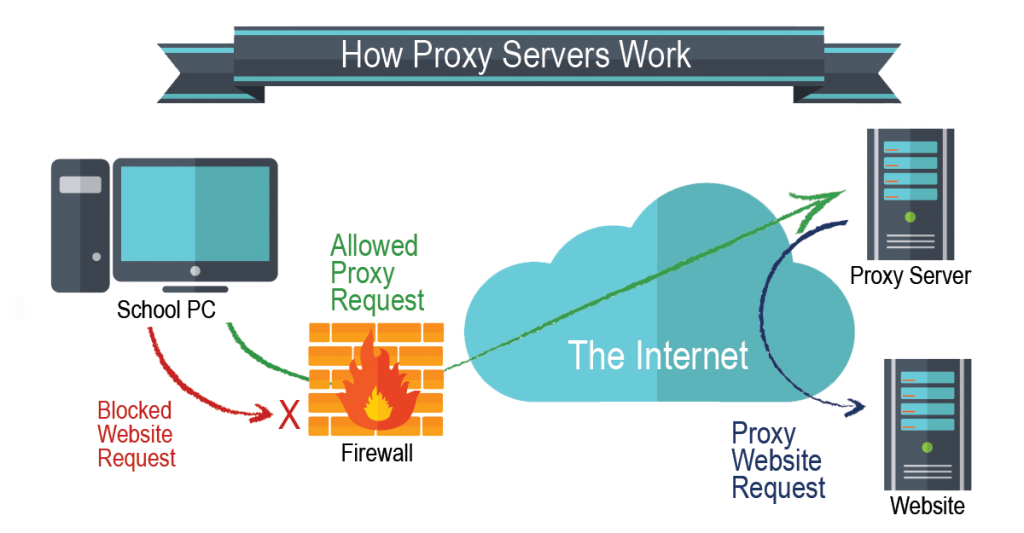
4. Making use of Proxy Servers for your Firewall
One of the web servers that can function as an intermediate between the internet and your device is a proxy server. It is quite ironic that a proxy server is what your school or company uses to restrict people’s access to the restricted sites.
In this case, when you make use of a proxy server to gain access to restricted sites that have been restricted by another proxy, it serves as the best example of beating others to the game.
Note that the paid proxies must be what you use to bypass firewalls. This is because free proxies will often bug you with adverts and are often not secure enough for you to use.
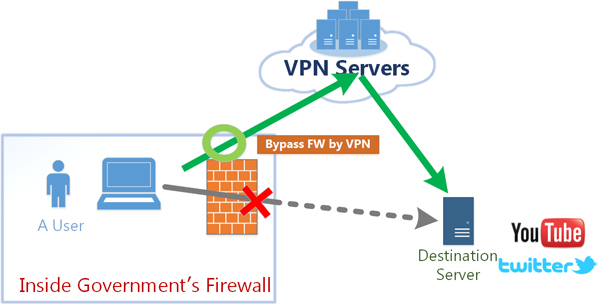
5. Making use of Virtual Private Network (VPN) for your Firewall
This is the last method of bypassing a firewall. Here, you will have to make use of a Virtual Private Network (VPN). VPN is one of the most effective solutions to circumvent a firewall.
What a VPN connection does is to alter your routing table. What this means is that the IP layer will route your outgoing traffics into the Virtual Private Network. The VPN now wraps the datagram of the IP into another packet of the Transmission Control Protocol. This packet will now be sent to the Virtual Private Network.
This way, your initial Transmission Control Protocol (TCP) packet will become anonymous to the IP layer. In addition, the moment this packet goes through the Virtual Private Network, it becomes unwrapped. After this, it will be sent to the last stage in its initial form.
This is used to generate the effectiveness of a tunnel that Virtual Private Networks are known for. When you send the TCP packet via the connection of the Virtual Private Network, you have successfully bypassed the routing rules and the firewall.
With this, you can now gain access to any site of your choice even if the website is under restriction on your local network. Just like what we discussed under proxies, you will have to use a premium (paid) Virtual Private Network if you want a better and more secured service such as no ad, pop-ups, and complete access.
Conclusion
This article has successfully examined the various methods of bypassing a firewall. A firewall is a software, hardware (or both) network security that you can use to track all forms of outgoing and incoming network traffic. It is used to block and activate specific traffic.
When your school or company restricts you from accessing a particular website, you can make use of the various methods we have discussed in this article to bypass the firewall and gain access to any blocked site you want to surf.